
When browsing the internet, your data packets travel across different networks, making it essential to ensure their privacy and security. VPNs are excellent for masking your identity and encrypting your connection, but what happens when you need to bypass firewalls and circumvent censorship? This is where the Stealth protocol comes in.
Stealth is a VPN protocol designed specifically to evade deep packet inspection (DPI) and help users stay anonymous in regions with stringent internet censorship. Whether you're in China, Russia, or any country with heavy internet restrictions, Stealth allows you to bypass government filters and unblock websites.
While most VPN providers don’t offer a dedicated obfuscation protocol, Windscribe includes Stealth as one of its six connection options. It’s designed to make your VPN traffic look like normal HTTPS web browsing, allowing you to bypass network restrictions and access the open internet securely.
In this guide, we’ll walk you through what the Stealth protocol is, how it works, and why it’s an essential tool for users in restrictive environments.
What Is Stealth Protocol?
Stealth VPN is a specialized VPN protocol designed to bypass censorship and evade detection on restrictive networks and VPN blocks. In countries like China, Iran, or the UAE, where VPN usage is heavily monitored or blocked, traditional VPNs are often detected through deep packet inspection (DPI), a technique used to analyze and filter internet traffic.
Stealth solves this problem by disguising VPN data as normal HTTPS traffic, making it nearly impossible for filters to tell the difference between a VPN connection and a regular secure website. This allows users to stay completely undetectable and maintain uninterrupted access and complete online privacy, even under strict surveillance systems and internet filters.
Stealth Protocol Explained
Under the hood, Stealth VPN is an OpenVPN tunnel enhanced with an additional layer of SSL encryption using Stunnel, an open-source library that wraps standard VPN traffic inside HTTPS. This process, known as VPN obfuscation, makes your encrypted VPN packets look like ordinary web browsing to firewalls and DPI systems.
Because Stealth mimics HTTPS, blocking it would mean blocking all secure web traffic – something most networks can’t afford to do. That’s what makes Stealth particularly effective for bypassing VPN bans and maintaining access on school, corporate, or government-controlled networks.
Unlike standard OpenVPN, Stealth can connect through 11 different ports, including port 443, the same port used by secure sites. Since port 443 is almost always open, Stealth can slip through firewalls and network filters that would normally block VPN traffic.
In short, Stealth VPN works by masking OpenVPN traffic with SSL encryption, turning it into something indistinguishable from normal HTTPS browsing. It’s the go-to protocol for users who need stable, undetectable connections in high-censorship regions or on restricted networks.
How to Set up Stealth Protocol With Windscribe
Setting up the Stealth protocol in Windscribe takes only a few clicks. Whether you’re on Windows, macOS, Android, or iOS, you can easily switch to Stealth within the Windscribe desktop or mobile app. Here’s how:
Step 1: Open the Windscribe app on your device.
Step 2: Go to Preferences. Click the menu icon (☰) in the top-left corner.
Step 3: Navigate to the Connection section, where all protocol settings are located.
Step 4: Set Connection Mode to Manual.
Step 5: Select Stealth from the protocol list.
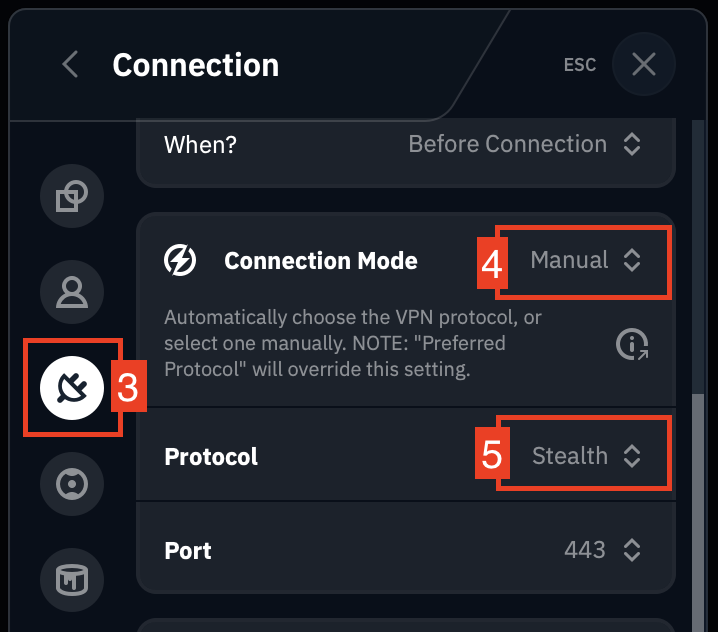
That's it – Stealth enabled!
Benefits of the Stealth Protocol
Stealth gets you online when nothing else works. It’s made for travelers, journalists, and everyday users who need a VPN that can slip past firewalls and VPN blocks. Here are the benefits of the Stealth protocol.
1. Bypasses Firewalls and Censorship
The biggest advantage of Stealth is its ability to evade deep packet inspection (DPI) and bypass firewalls that block normal VPN traffic. It does this by wrapping your connection inside SSL encryption, the same security used by HTTPS sites. To the network, your VPN traffic looks just like regular browsing, meaning you can access the open internet even on heavily restricted networks..
2. Maintains Privacy in High-Surveillance Regions
Stealth keeps your activity invisible to network monitoring systems. In countries where ISPs and governments actively track or throttle VPN usage, Stealth ensures that your connection looks ordinary and doesn’t trigger alerts. By mimicking HTTPS, it hides both your VPN handshake and the type of encryption being used, keeping your identity, browsing activity, and destination servers fully private.
3. Works on Networks That Block Other Protocols
When other protocols like WireGuard or OpenVPN UDP can’t connect, Stealth usually can. Because it uses port 443 (the same one used for HTTPS), it works almost anywhere. From hotels and airports to countries with strict censorship laws, Stealth is the protocol that usually still gets through when others can’t.
4. Provides Secure, Encrypted Connections
Stealth protects your traffic twice. Your data is encrypted once through OpenVPN, and again through SSL encryption with Stunnel. This layered approach means even if someone intercepted your data, all they’d see is random, unreadable HTTPS traffic.
When to Use Stealth Protocol?
Stealth isn’t the protocol you’ll use every day, but rather the one you turn to when other VPN protocols can’t connect or when you’re on a network that blocks VPNs.
Use Stealth when:
-
You’re in a country that restricts VPN use (like China, Iran, or the UAE).
-
You’re on public Wi-Fi that blocks or throttles VPN connections.
-
You’re connected to a corporate or school network with strict access controls.
-
Other protocols, such as WireGuard or OpenVPN, fail to connect.
-
You want an extra layer of privacy by making your VPN traffic look like regular web browsing.
-
You want to experience complete internet freedom and circumvent censorship.
Frequently Asked Questions About Stealth VPN Protocol
What is the main purpose of the Stealth VPN protocol?
The Stealth protocol is designed to bypass firewalls and censorship by disguising VPN traffic as regular HTTPS traffic. It is used in regions or networks where VPN connections are blocked or restricted, allowing users to stay connected and maintain privacy when other protocols fail.
How is Stealth different from OpenVPN or WireGuard?
Unlike OpenVPN or WireGuard, which can be detected by deep packet inspection (DPI), Stealth adds an extra layer of SSL encryption using Stunnel. This extra layer hides VPN traffic inside standard HTTPS, making it virtually undetectable to filters and inspection systems.
Is the Stealth protocol slower than other VPN protocols?
Yes. Because Stealth adds an extra layer of encryption for obfuscation, it can be slower than WireGuard or OpenVPN. However, it is more reliable on networks that block or throttle VPN traffic, making it the preferred choice when connection stability is more important than speed.
When should I use Stealth instead of other protocols?
Stealth is best used when you are on a network or in a country that restricts VPN usage, such as China, Iran, or the UAE. It is also useful on public Wi-Fi or corporate networks that block standard VPN connections. For everyday use, faster protocols like WireGuard are generally recommended.
Does Stealth work on all devices?
Yes. Stealth can be enabled on all Windscribe desktop and mobile apps, including Windows, macOS, iOS, and Android. To activate it, go to Preferences, open the Connection tab, set the Connection Mode to Manual, and select Stealth as the Protocol. The browser extension does not support Stealth.
Is Stealth safe to use?
Yes. Stealth uses AES-256 encryption within an SSL tunnel, providing two layers of security. This ensures that even if your connection is intercepted, your data remains unreadable and your VPN activity stays hidden.
Does Stealth work for streaming or torrenting?
It can, but it is not optimized for high-speed activities. Stealth is designed primarily for privacy and accessibility, not for maximum performance. For streaming or torrenting on unrestricted networks, protocols like WireGuard or OpenVPN may offer better speeds.
Is the Stealth Protocol Right for You?
The Stealth protocol isn’t the fastest option in your VPN toolkit, but it’s the one that keeps working when others can’t. If you often connect from countries with heavy censorship, use public Wi-Fi where VPNs are blocked, or simply want an extra layer of privacy, Stealth is the right choice.
Ready to try Stealth? With Windscribe, enabling Stealth takes only a few clicks, and it’s available on all our desktop and mobile apps. Download Windscribe today and protect your connection.
Contact Support
